Tonya Mead, PhD, MBA, M.Ed, CHFI, CFE, PI
Now more than ever before, k-12 public and private school systems and institutions of higher learning are relying upon advancements made in educational technology for the delivery of classroom instruction. With the global CoVid-19 or the Coronavirus pandemic, this demand has never been greater.
This is welcome news for cyber security enthusiasts. Are you preparing to meet a potential client in the education sector and you need a primer on making a case for hiring you as a certified ethical hacker or computer hacking forensic investigator ? This case study will summarize the cyber security and data privacy threats associated with the lack of stringent internal controls for monitoring educational technology systems installed by nations, states, localities and individual school campuses.
Coronavirus and Zoom Hack
Because of the Coronavirus, k-12 schools, colleges and universities are turning to low cost, open-sourced and proprietary platforms to provide online distance learning. Unfortunately, as one might imagine, the threat of hacking is rampant.
A few days ago, the USC campus and local school districts were utilizing the Zoom video-conferencing platform which had been hacked. The perpetrators spread racist remarks and broadcast pornographic images throughout the system to disrupt scheduled meetings.
Alexa and the Urgency of Now
Alexa disclosed to another party, a private conversation that was held by a family within the confines of their own home. There are widespread concerns that the private information of school students could be compromised without adequate emphasis and investment in cyber security instruments, protocols, systems and personnel.
Abstract: Educational Technology in the Classroom: Positive Results
Much like Alexa, Zoom, and GoTo Meetings for instance, the use of data and technology holds the promise of delivering online and distance learning, helping students gain mastery of subject matter content, and supporting professionals during remote work. A six-year study completed by the State Educational Technology Directors Association (SETDA) found that classroom incorporation of technological tools led to “positive academic results” [A]. Gill, Borden and Hallgreen found these uses of data-driven decision making: policy, resource allocations, and evaluations of teacher effectiveness and program quality [p.5].
Other articles of interest
- Post- WTF? CDI says don’t worry about data threat in schools
- Post- Alexa and the threat to privacy in schools
- Post- Smartphone use, sleep and your child
- Post- Hack to prove enrollment
- Post- Cyber scammers target schools
- Post- Botnet grade in education- graph
- Post- Botnets and identity theft in education
- Presentation- The exploitation of minors to gain confidential information
- Post- Internet filters and monitors in schools
- Post- Summertime, kids and cyber threats
- Post- College Tech Cheats and Social Media
Educational Technology Investments
Globally, Fortune projects that spending in educational technology will reach $19 billion by 2019 [1]. This is 20 percent higher than BMO Capital Markets estimates of $15 billion [2].
Investments: United States
In the U.S., education institutions spent about $4.7 billion at elementary and secondary levels and $6.6 billion on the post-secondary level for information technology in 2015 [3].The reasons for increased investment? According to the U.S. Department of Education,
“Technology ushers in fundamental structural changes that can be integral to achieving significant improvements in productivity. Used to support both teaching and learning, technology infuses classrooms with digital learning tools, such as computers and hand held devices; expands course offerings, experiences, and learning materials; supports learning 24 hours a day, 7 days a week; builds 21st century skills; increases student engagement and motivation; and accelerates learning” [3, para 1].
Investments: Europe
The U.S. is not alone. In 2016, the German Minister of Education committed $5.0 billion (the equivalent of $5.5 US Dollars) to support digital learning throughout 40,000 schools [4]. This is significant as “Germany spends more on education than other European countries in absolute terms” according to the Goethe Institute [5].
Venture Capital Investments
Even venture capitalists have forecast the prospects for higher than average earnings by infusing $1.87 billion of capital into the education sector 2014 [6]. The magnitude and speculative expectations may present added risk for cutting corners, reducing emphasis on data privacy, and eliminating stringent internal controls.
The Need for Educational Technology Tools and Products
In the past decade, the digital frontier has projected onto the educational landscape of underperforming schools, tight budgets, disengaged students, and overwhelmed instructors, the promise of improved performance, targeted interventions, reduced costs, and greater efficiencies.
Threats
Cheerleaders of the rapid adoption of advanced technologies utilized to increase the capture, analysis, and use of data, may have overlooked (in haste) the accompanying vulnerabilities [7]. In reviewing the Ponemon research and analyzing incidents in the education sector, this author as observed the following phenomena.
(1) As student data accumulates, the risk of data breaches and unintentional disclosure of personally identifying private information (PIPI) increases exponentially [8] [9].
Educational entities, unlike the private sector, have not yet recognized the threat and have not taken precautionary steps to secure personally identifying private information. This is not the case in the private sector, whereby proprietary intellectual property is considered an asset to be guarded at all cost. This brings another interesting observation. Pouncing on opportunities, criminals in previous years have identified the education sector as the number one target for malware. From January to June 2010, “44% of all malware infections hit schools and universities” [10]. While the education sector has not remained at the top of the criminal’s target list in 2015, there are trends showing that the threat is still very real [11]. Michael Oppenheim of FireEye, an internet security firm, estimates that 550 universities had experienced some type of data breach from 2006 to 2013, exposing confidential student and staff information [12].
(2). Utilizing Wortley’s Situational Factors as a basis, criminals target systems believed to be less guarded (educational entities) than others.
Due to the pervasiveness of the threat to the exposure of confidential information, the European Union established the General Data Protection Regulation (GDPR). This law mandates that businesses must protect consumer data by default, not as an opt in feature [13]. In the United States, Congress proposed a Student Privacy Bill in October 2017, making data security mandatory [14]. While in its first stage of the legislative process, if adopted as law, it will strengthen the enforcement provisions of the Family Education Records Protection Act [15].
Why was the legislation necessary? SANS Institute [16] reported upon a Computer Weekly survey of 638 public and private sector respondents. They discovered “in more than 63% of security breaches identified by respondents, human error was the major cause. Only 8% were purely technical failures.” These numbers reveal that the human element is the weakest part of any security system [17]. This is particularly true for the education industry [18].
(3) The lack of Lack of Cyber
Security, Information Technology, Data Privacy Expertise and Training make
unsuspecting employees in the education sector vulnerable to malware.
Almost 15 years ago, the Federal Trade Commission as cited by Willis and Raines
critiqued the antiquated systems and poor conditions of technology in education
[19].
“There are thousands of buildings in this country with millions of people in
them who have no telephones, no cable television, and no reasonable prospect of
broadband services. They’re called schools.” While computer accessibility has
greatly improved, the need to update educator knowledge with technology
advances is critical. Further, the lack of educator training on access
management and maintenance is an impediment to data quality and information
security.
Research by Yamamoto, Penny, Leight and. Winterton “suggests that pre-service teachers should be prepared to teach with technology, rather than just learning about technology”[p. 30]. These findings are supported by an International Society for Technology in Education (ISTE) study showing that “learning with technology is more important than learning about technology” [20, p. 16].
In a survey of 90 teacher preparation programs for The American Association of Colleges for Teacher Education, faculty respondents reported that 58 percent of teacher candidates were prepared to use computers as instructional aids in the classroom. During the same study, however, just 29 percent of the teacher candidates, when posed the same question felt ready to teach with computers [21]. To elucidate the reason for failure to prepare future educators, the Congressional Office of Technology Assessment hypothesized that there exists a “lack of expertise of many education school faculty” with computers .
(4) Educator preparation programs have failed to provide ample and robust training in cyber security and information technology.
In addition to inadequate preparation prior to hire, educators lack professional on-the-job training while employed. Borthwick and Pierson site a study by Bond (1998) finding that educators in Asian countries devote up to 60 days per year in professional development training [22, p. 11]. On the other side of the globe, Brown (2003) asserts (as cited by Borthwick, et al) that “new teachers in American public schools, on the other hand, are often turned loose in their classrooms, only to be heard from again on the day they quit” [22, p. 9].
Goldman, Cole, and Syer [23], found that computer labs are prominent in most schools. Computers are situated in almost every classroom. Nonetheless, teachers have not made much use of technology. Trotter estimated that almost 40 percent of teachers have not integrated computer use into lesson plans at all [24]. By 2003, a study financed by the Gates Foundation recorded little change [25].
A decade later, an Information Technology Panel identified “updating IT professionals’ skills and roles to accommodate emerging technologies and changing IT management and service delivery models” as the top priority for the education sector [26].
(5) Lack of professional development opportunities in cyber security, information technology and data privacy increase the likelihood of data exploits in the education sector.
The exertion of pressure to utilize computers in the classroom and to make data analysis available for the realization of gains in student learning weighs heavy upon educators. At the same time, the increased demand for student, parent, and public access to private information through vulnerable networks makes for an environment ripe for exploitation. Plante Moran has this to say,
“typically, the greatest security weakness of school districts is a lack of IT resources coupled with the need to provide greater access to the network…. In general K-12 IT systems tend to spend less on sophisticated protections than those of large corporations, making them easier to penetrate.” [ p.22].
(6) The absence of cyber ethics training increase the likelihood of human error.
“Banks and governments could be ‘brought to their knees’ by computer hackers because of the “weak link” represented by large numbers of staff who aren’t properly trained in cyber security” remarks Professor Benham, visiting professor in cyber security management at Coventry University [27, para 1]. This statement is applicable to educational institutions in the United States.
The lack of a formalized ethics training in education greatly heightens threats to cyber security. “To fully understand why the field of cyber ethics is important, one must first understand how to approach the study of general ethics” (Thorson, 2011) Inadequate ethics courses in professional educator certification programs, lenient enforcement of FERPA privacy protections, and inconsistencies in collection and reporting standards for PIPI data present conditions for increased risk for crime and self dealing. The National Cyber Security Alliance, for example, studied educator perceptions. Less than 25 percent of the respondents felt comfortable advising students on self protection against cyber predators, bullies, and identity theft [28].
(7) Undisciplined internet use linked to increased incidents of malware and identity theft.
The National Bureau of Economic Research [29] analyzed 2003 to 2011 data from the American Time Use Survey showing that the typical American spent 13 minutes on the internet each day for leisure. Conversely, 1,300 college students reported spending 100 minutes daily [30]. In like manner, about 60 percent of the faculty reported weekly internet usage of four to 19 hours [31]. Beyond this mid-range category of faculty respondents, “another 40 percent reported being online for 20 or more hours, approximately three hours or more per week, or three or more hours per day” which is in excess of the norm for faculty users [31, p. 4].
In Europe, Eurostat reports that “almost four out of every five (79 %) young people used a computer on a daily basis in 2015, which was 16 points higher than among the whole population (63 %).” [51] Incidentally, “the highest rates of daily computer use among young people were recorded in Estonia (90 %), Poland (89 %), the Czech Republic, Latvia and Slovakia (all 88 %). “ [52].
In comparison to the typical American, educators and college students spend more time on the internet, making them (and the networks used) targets for malware. Malware is utilized for the purposes of grand theft and identify theft. In 2010, hackers stole $996,000 by inserting a virus into the authorization codes used by the controller at the University of Virginia. The scammers fraudulently wired money from the university’s BB&T bank account to the Agriculture Bank of China [32].
Lack of pre-service and embedded training for U.S. based educators, pose significant threats. Training in the instructional uses, limitations, as well as the risks associated with computer technology is paramount. The American Association of School Administrators analyzed reports of internet users receiving fraudulent emails. They found that “70% of internet users have unintentionally visited a spoofed website and that more than 15% of spoofed users admit to being phished.” Professional development aimed at preventative measures can do much to thwart the unintentional release of confidential student information as well as unauthorized access to accounting and finance systems. Fraudulent emails are hard to detect with basic spam-filtering because they are designed to look like legitimate emails.
(8) Adopted technology standards not put into practice thereby increasing risk exposure.
The National Council for the Accreditation of Teacher Education Programs adopted technology standards for teachers in 1998 [33]. The Association of School Administrators, in 2001. Yet, a coalition of organizations such as the Data Quality Campaign, American Association of Teacher Education Programs, the Council of Chief State School Officers, the National Association of (NASDTEC), the National Council on Teacher Quality, the National Education Association and WestEd determined these measures have not been applied consistently. The coalition has advocated for “teacher data literacy through state policy” while promoting and incentivizing ongoing technical training [34, p.1].
(9) Inconsistencies in communication from the top.
The lack of clear messaging increases environmental vulnerabilities to cyber and computer assisted crime. Jeffrey concluded that misconduct has a higher probability of occurring when victim organizations lack positive social reinforcers for employee emulation. This involves positive social pressure from peers and role modeling to alleviate inconsistencies in spoken, written, and nonverbal communication concerning the protection of confidential information.
Brown, Trevino and Harrison postulate that the highest caliber leaders create and support ethical decision-making by communicating and modeling high ethical standards. “These top managers create and maintain an ethical culture by consistently behaving in an ethical fashion and encouraging others to behave in such a manner as well” [35]. The Association of Certified Fraud Examiners takes the concept a step further and says, “employees will do what they witness their bosses doing” [36]. McCabe, Trevino and Butterfield found inherent within the expectation of role modeling and communication was the development of conduct codes that are clear, provide unambiguous language regarding acceptable behaviors and expected procedures, and are enforced.
(10) Porous internal controls increase the probability of internal hacks for personal and financial gain.
The failure of management to address the complexities inherent in the validation of disparate data from multiple sources, differing file formats and structures is immense. The enormous task of data maintenance stored in hardware systems customized by multiple vendors for differing uses and the integration of information entered into software applications exacerbate data manipulation allegations. These problems span data used for finance/accounting, enrollment/registration, institutional development/research, exam administration/testing, and academic scheduling/grading.
For instance, students have filed lawsuits ranging from $5 million to $40 million alleging the payment of tuition for classes that were never held and the falsification of records to “enroll them and keep them enrolled so that government grant and loan dollars would keep flowing ”[37][38][39]. Harvard University conducted an inquiry in 2010 of scientific misconduct concerning problems of “data acquisition, data analysis, data retention and the reporting of research methodologies and results” [40]. An El Paso Superintendent was sentenced to four years imprisonment, $56,600 in fines, and $180,000 in restitution for contract fraud and data tampering [41]. The Ohio Auditor charged Columbus City Schools District Superintendent for presiding over a culture of data manipulation alleging changed grades, deleted absences, and falsified dropout data. Auditors in Washington, DC found that schools failed to maintain internal controls for graduation and special education [43] data. Data tampering extends to scientific research with estimates up to 65% of retractions “due to misconduct” [44]. The failure of universities to control data led to overpayments of $222 million to 42,000 distance learners, who did not earn any academic credits during the payment period” according to the U.S. Department of Education, Office of Inspector General.
“Big data represents all kinds of opportunities for all kinds of businesses, but collecting it, cleaning it up, and storing it can be a logistical nightmare” [45, para 1]. The challenge according to the Developer Network is to:
“extract the data, often from a variety of disparate systems, to transform that data, so that it is uniform in terms of format and content, and finally to load the data into a warehouse where it can serve as a basis for future business intelligence needs. It’s very important that the integrity of the data is maintained” [45, para 4-5].
“Twenty-six states have designed and built or upgraded their data warehouses, or are in the process of doing so” [147, p. 1]. In reading through allegations of data tampering in the education sector, however, it becomes clear that much needs to be done to enhance the internal quality control measures (extraction, transformation, and loading) necessary to ensure data integrity.
(11) The negligent disclosure of student confidential information is on the rise.
Along with the promised advantages of improved performance, targeted interventions, and greater efficiencies; increased vulnerabilities exist. The unintentional disclosure or data breach of confidential information is a critical vulnerability [46]. The causes of data breaches are varied. Sources range from database hacking, the accidental emailing of confidential information from a secure file to the wrong email address, and obtaining unencrypted files from a stolen laptop [47]. The FBI estimates that 85 to 97 percent of intrusions remain undetected. In a study of 390 attacks, less than 10% of the managers reported the attacks. In the education sector,
“breaches can run the gamut from students
hacking into school databases and changing their grades to instigating a denial
of service attack to stop electronic testing to a major infiltration by
cybercriminals who steal personally identifiable information such as Social
Security and credit card numbers…Their multiple buildings are at times open to
the public, allowing anyone to connect a device to their network, which makes
the network incredibly difficult to secure” [48, p. 21-22].
Conclusion
In reading this premier, hopefully,
you have identified the need for your certified ethical hacking and/or computer
hacking forensic investigator expertise and developed ideas for how it can be
applied in the education sector. The
application of your critical skills in this sector should be in high demand.
The only barrier to success is your ability to communicate the dangers in leaving
the possible entry points open for exploitation. With your hard work, I’m sure
you’ll endeavor to join me in keeping them closed.
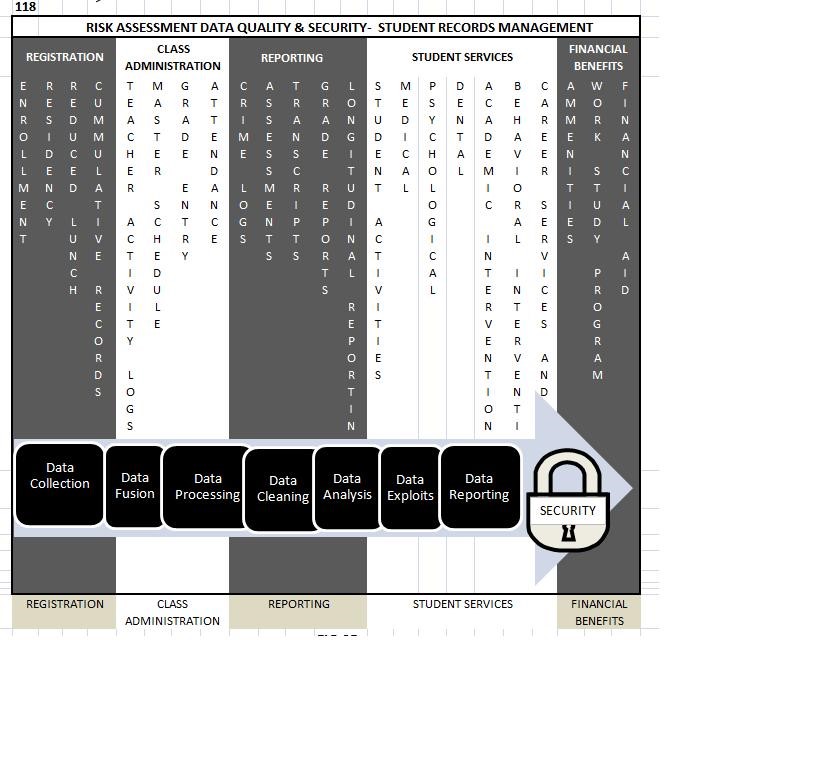
Image: Myriad Data Points Vulnerable to Exploitation [50]
About Tonya Mead
Tonya J. Mead, PhD, MBA, M.Ed, CHFI, CFE, PI, is the founder of Shared Knowledge LLC a private security and detective agency. Dr. Mead, formerly a certified K-12 Administrator and School Psychologist, is author of Fraud in Education: Beyond the Wrong Answer and president of Shared Knowledge, LLC https://ishareknowledge.com If you like her work, please support her at Patreon.
Non Hyperlinked References
B. Gill, B.C.
Borden and K. Hallgren, “A Conceptual Framework for Data-Driven Decision Making,” Mathematica
Policy Research. Princeton, NJ.
Reference Number 40019.190. June 2, 2014.L. Ponemon, “What does a data breach
cost companies?” Ponemon Institute, LLC, Traverse City, MI, 2005.
J. Yamamoto, C. Penny, J. Leight and S. Winterton, Technology Leadership in Teacher Education:
Integrated Solutions and Experiences. Hershey: NY. IGI Global, 2010.
“Teachers and Technology: Making the
Connection,” US Office of Technology Assessment and Congressional Office
of Technology Assessment. Washington, DC. GPO Rep. No. 052-003-01409-2, 1995.
Plante
Moran, Southfield, MI, “The Technology Imperative: Staying Ahead of the Curve
in the Classroom,”(n.d.).
C.R. Jeffery, “Criminal Behavior and Learning Theory,” Criminal
Law, Criminology & Police Science, Vol 56, Issue 3, Article 4, p.
294-300, Fall 1965.
M. Brown, L. Trevino, L. and D. Harrison,
“Ethical leadership: A social learning perspective for construct development
and testing.” Organizational Behavior and
Human Decision Processes, 97(2), p. 117-134, 2005.
D.L.
McCabe, L.K. Trevino and K.D. Butterfield, “Academic
integrity in honor code and non-honor code environments,” Journal of Higher Education, 70, p. 211-234, 1999.
